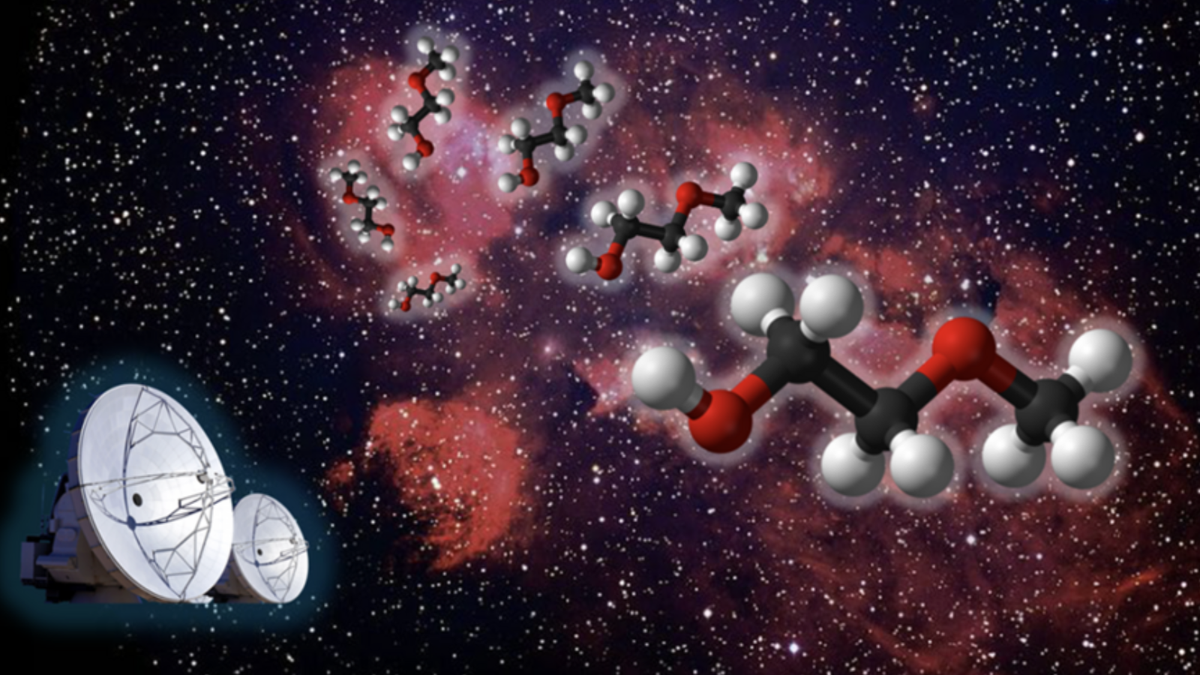
Los científicos han descubierto una partícula espacial hasta ahora desconocida mientras examinaban una región relativamente cercana al nacimiento de estrellas...
Usain Bolt, el mejor velocista de todos los tiempos, encabezará las leyendas del deporte que asistirán a los Laureus World...
fénix - Once republicanos que presentaron un documento al Congreso declarando falsamente que Donald Trump derrotó a Joe Biden en...
Gómez, de 49 años, esposa del primer ministro español, no ocupa cargos públicos y mantiene un perfil político bajo, informó...
Hayes instó a realizar inversiones agresivas en medio de la desaceleración del mercado. Hayes vio a Bitcoin como una cobertura...
Resumen del lanzamiento: Desplácese hacia abajo para revisar la cobertura en vivo del despegue del cohete SpaceX Falcon 9 el...
Xavi Hernández, entrenador del Barcelona, ha decidido quedarse en el club hasta final de contrato ... Que finaliza en 2025...
manzana lanzada La tercera versión beta de iOS 17.5 Para los probadores beta públicos el miércoles, un día después de...
Anchorage, Alaska - Uno de los pilotos de un avión que transportaba combustible informó de un incendio en el avión...
Desde primera hora de la mañana quedó claro que el presidente del Gobierno español, Pedro Sánchez, estaba dolido por la...